WinDbg - Reverse Engineering/Debugging
This tool is my most favorite, it provides complete functionality for enthusiasts and is for free. There is a wide range of extension and commands for viewing data structures, memory addresses and call stacks. It can be used for both reverse engineering and debugging BSODs (Blue Screens of Death).
There is good documentation for WinDbg for finding hidden rootkits, examining data structures and looking at raw memory. Most of this information has been used in my blog for writing tutorials and adding my own information to. It can be used for static analysis and real-time analysis.
Link - Windows Driver Kit (WDK) and Debugging Tools for Windows (WinDbg)
OllyDbg - Reverse Engineering (User-Mode)
OllyDbg is a great tool for reverse engineering user-mode programs. This is a another standard tool if you wish to examine malware or would like to learn the PE structure. This tool is for free, and again is there is great documentation for learning how to use it. Please check the Blogroll section for such blogs.
The data structure being viewed is the _PEB data structure, which is stored at offset 0x30 in the FS register for x86 systems. It is primarily used for static analysis.
Link - OllyDbg v.1.10
IDA Pro - Free Version
This tool is used for reverse engineering, and widely used by professionals to my knowledge. This is a very powerful tool, and be used to examine libraries in the IAT and EAT, look at strings stored in memory and assembly instructions. There are tutorials available on their website.
Link - IDA: About
Analyze It!
This tool is great for displaying information about a specific binary file (static analysis).
I could only find the program hosted on Softpedia, but I'm sure that there wasn't any other programs bundled with the installation package.
Link - Analyze It! Free Download (Softpedia)
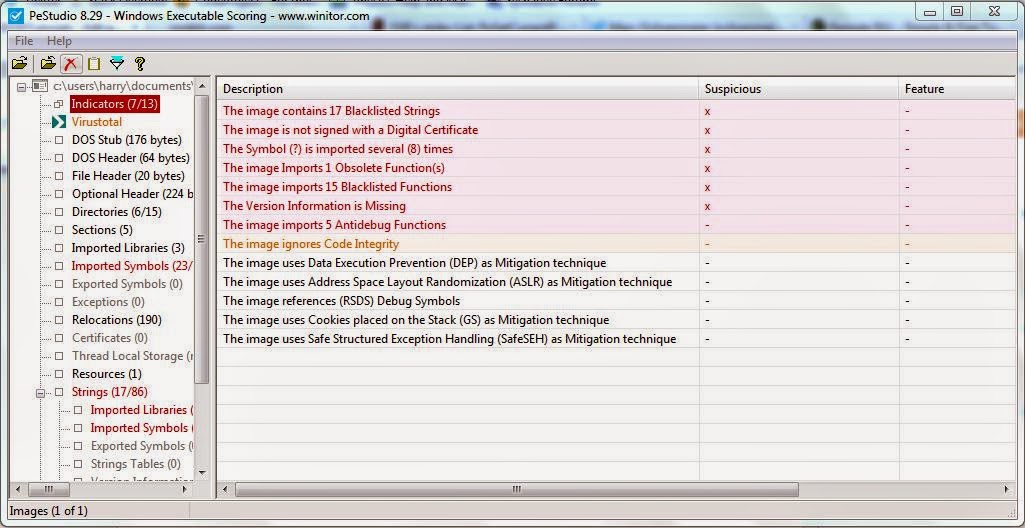
PeStudio
This is tool provides the same features as the other program, but with a simpler and cleaner UI and is easier to use in my opinion. It also has VirusTotal integration.
Link - PeStudio
Twitter -
Hook Analyzer
The program enables you to hook to a certain active process, and then pull information from that process. It only works with Ring 3 (User-Mode) processes to my knowledge.
PE Bear
PE Bear is another static analysis tool for examining PE files, you can view file signatures and view packers which have been used.
Link -PE Bear Blog
WinHex
WinHex can be used for examining the hexadecimal format of files.
Process Explorer
Process Explorer is a Microsoft produced tool, which can be used for finding general information about active processes. It has Virus Total integration.








No comments:
Post a Comment